BetterTTV (BTTV) is a web browser add-on popular among Twitch.tv users. It offers many features to enhance the video streaming and viewing experience such as emoticons and improved chat history. As of writing, the number of weekly active BTTV users given by Chrome Web Store is over 1.2 million.
Twitch.tv is a live streaming video platform focused on video gaming. According to Twitch’s 2016 retrospective the service hosted 2.2 million unique streamers. Although BTTV is a third-party add-on, it is often considered “must have” for Twitch users. It is developed by NightDev.
The Chrome add-on had a stored XSS vulnerability which allowed JavaScript to be injected in Twitch chat messages. An attacker sending a malicious chat message could execute code in web browsers of BTTV users. No interaction from the victim was required.
The script would run in Twitch.tv’s context, meaning the attacker could take actions on viewers’ or the streamer’s behalf. Exploitation possibilities included e.g. stealing the stream key to push unauthorized content in the video stream, modifying settings or profile contents, or reading and sending Twitch private messages.
Participating the chat requires a Twitch account but registration can be done anonymously. Popular Twitch streams often have tens of thousands of simultaneous viewers so sending one chat message could compromise many users.
Details
The add-on works as a content script, defined in the extension’s manifest.json as:
{
"browser_action": {
"default_popup": "settings.html"
},
"content_scripts": [ {
"all_frames": true,
"js": [ "betterttv.js" ],
"matches": [ "*://*.twitch.tv/*" ]
} ],
"description": "Enhances Twitch with new features, bug fixes, and reduced clutter.",
"homepage_url": "https://www.betterttv.com",
// ...
One of the enhancements BTTV offers is chat image link preview. The content script generates some hidden HTML for each image link it detects in the chat and shows it when the link is hovered over. The code generating this HTML didn’t sufficiently validate the link URL. A specially crafted image link could be used to inject any HTML in the chat.
A proof of concept chat message that would show a JavaScript alert box:
https://a/b.jpg?a><script>alert('hello');</script>
Result for a viewer:
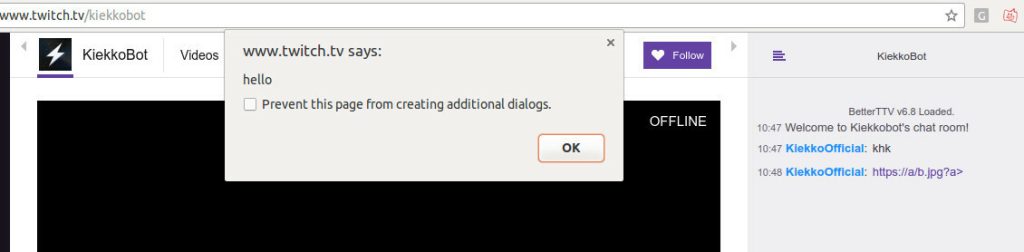
Injected elements as seen in Developer Tools:
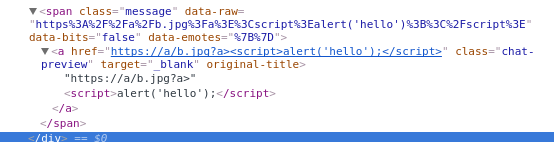
Another proof of concept was made to confirm that the attacker could read the Twitch inbox and retrieve the stream key with an AJAX request.
The bug was only tested on Google Chrome but other browsers supported by BTTV may have also been vulnerable.
Vendor response
The bug was found on February 17, 2017 and reported to NightDev, who fixed the bug within an hour. The fix was deployed on NightDev’s servers. The client-side add-on doesn’t need to be updated.
Credits
The vulnerability was found by Jouko Pynnönen of Klikki Oy, Finland.